- CramHacks
- Posts
- CramHacks Chronicles #92: Weekly Cybersecurity Newsletter!
CramHacks Chronicles #92: Weekly Cybersecurity Newsletter!
What $270,000 of bug hunting open source gets you, Post-quantum cryptographic scanner pqscan, mcp-remote RCE, North Korean malicious npm packages
Hello, and Happy Monday!
I’m in grind mode. I’ve barely been outside lately, but my excuse is that I ran out of contact lenses and moving around while wearing my glasses gives me migraines. Tomorrow I’ll be going to the optometrist and speaking at the local OWASP meetup. I’ve also finally booked my travel for Vegas next month, hope to see a bunch of y’all there!
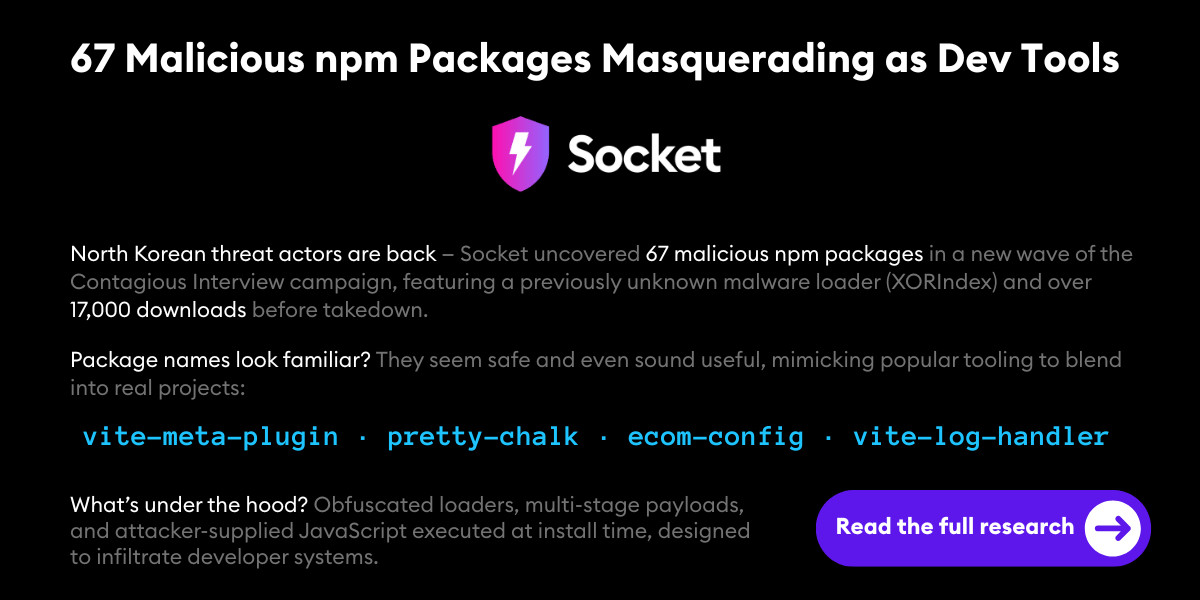
Check out Socket’s latest blog post on North Korean threat actors leveraging malicious npm Packages. Given how active they are in this space, maybe I should ask, are any of you subscribers a North Korean package malware author? 😅
Get the full list of malicious packages, IOCs, C2 infrastructure, and loader behaviors in this detailed breakdown of North Korea’s most persistent open source supply chain campaign to date. ➜ Read the research
Introducing AI agents and tools in AWS Marketplace
“AWS Marketplace now offers AI agents and tools from AWS Partners, allowing customers to find and buy third-party AI agent solutions with streamlined procurement and multiple deployment options.”
Critical RCE Vulnerability in mcp-remote: Threatens LLM Clients
Jfrog’s Or Peles discusses CVE-2025-6514, a vulnerability in the popular open source mcp-remote project. The project enables local MCP Clients that only support local servers, to connect to a Remote MCP Server. The baked-in auth support triggers the server to send an authorization_endpoint response value, which is opened by the client for the user to authenticate. Via a MiTM attack, a malicious actor can manipulate the value and leverage the file URI scheme to achieve code execution on Windows clients e.g., file:/c:/windows/system32/calc.exe?response_type=code.
Cyber Resilience Act: curl project receives risk assessment request
“As part of our ongoing efforts to comply with the EU Cyber Resilience Act (CRA), we are currently conducting a cybersecurity risk assessment of third-party software vendors whose products or components are integrated into our systems.”
👋 I can’t begin to imagine how I’d react to a message like this as an open source maintainer. Merriam-Webster says a Vendor is “one that vends : seller.” As per Daniel, the project has no contract with the f500 whom submitted the request. I wonder, how many dollars are being wasted by this entity to impose these requests on open source project maintainers? 💸
Scanning for Post-Quantum Cryptographic (PQC) Support
Anvil Secure has launched an open-source tool pqcscan, that can determine whether SSH and TLS servers support PQC algorithms.
👋 Can’t wait for 2030, when every pentest report will include a long list of services lacking PQC support 🤦.
Bug Hunting at Scale
In preparation for my AppSec Village talk, I’ve been reviewing data relevant to scaled bug hunting in open source software (OSS). One such example of this is Alpha-Omega, an OpenSSF-associated project funded by Microsoft, Google, Amazon, and Citi.
Between 2023-2024, OpenRefactory was granted $270,000 “for the purpose of reporting security vulnerabilities at scale in open source projects and working with the maintainers to get those vulnerabilities fixed.” The scope consisted of scanning the top 10,000 Java/Python open source projects using their proprietary Intelligent Code Repair (iCR) tool and the Omega Analyzer. The scope focuses on the following security categories:
SQL Injection
Cross-Site Scripting (XSS)
Command Injection
Path Manipulation
Deserialization
XML External Entity (XXE) Injection
Omega Analyzer was a suite of 20+ scanners, but it hasn’t received a commit in over 2 years, so I suspect this was not used by OpenRefactory. Notes from early-on in the project suggest that the Analyzer produced too much noise.
Fortunately, this project included monthly updates that were recorded and are publicly available. 2023 & 2024
In the end, after ~18 months, the results included:
10,250 projects analyzed
Python: 9,817
Java: 216
Go: 217
299 total bugs
Python: 216
Java: 48
Go: 35 (no notes for why Go was suddenly included)
55 high severity bugs (language breakdown wasn’t available 🤔)
One disappointing note is that I’ve only come across two published security advisories for the submitted bugs.
It begs the question, was it worth it? But I can’t answer that 😄. With the limited information I’ve reviewed, I’d argue that yes it was worth it, but only as an experiment. For now we know that it isn’t worth it. What feels apparent is that the scope should’ve been more carefully considered and defined. E.g., Which top 10,000 projects? At what point in time were the downloads compared? What download counts were used, and when did that evaluation occur? Which version of these projects was OpenRefactory to scan? The latest on GitHub? The latest official release? All stable releases?
In January 2024: the notes specified versions to assess “We will concentrate on the last five release branches of each of the projects.”
Until Next Time! 👋
Hey, you made it to the bottom – thanks for sticking around!
Questions, ideas, or want to chat? Slide into my inbox! 💌
Don’t hesitate to forward if someone could benefit from this.
See you next Monday!
-Kyle
P.S. CramHacks has a Supporter tier! You can upgrade here to support CramHacks and its free weekly content 😃.